Bug Bounty Program
📢 Submit your reports and find full details on our Hackenproof page: 🔗 Backpack Web & API Bug Bounty @ Hackenproof
Rules
Rewards are categorized into five tiers based on the severity of the identified vulnerabilities.
The reward amounts are as follows:
Critical: $10,000 - $100,000 USD
High: $5,000 - $10,000 USD
Medium: $500 - $5000 USD
Low: $50 - $500 USD
Upon acceptance of your bug or vulnerability report, rewards will be disbursed in USDC. Please note that the threat level will be assessed by the Backpack security team, and Backpack reserves the sole discretion to determine whether a report meets the reward criteria.
Scope of Vulnerabilities
The following modules are within the scope of the bug bounty program:
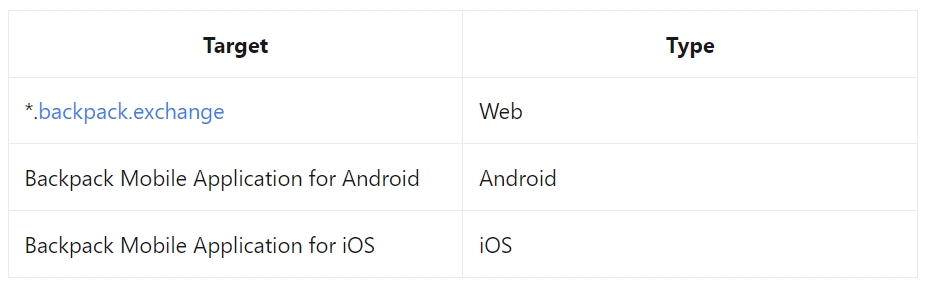
Criteria
Reports should focus on the following types of vulnerabilities:
Issues with business logic that may result in the loss of user assets.
Payment manipulation.
Remote code execution (RCE).
Leakage of sensitive information.
Critical OWASP issues such as XSS, CSRF, SQLi, SSRF, IDOR, and similar vulnerabilities.
Other vulnerabilities that may result in potential loss.
Exclusions
The following issues are not within the scope of the bug bounty program:
Theoretical vulnerabilities that have not been proven.
Flaws in email verification codes, expired password reset links, and password complexity policies.
Clickjacking and UI redirection with minor security impact.
Vulnerabilities in third-party applications or software.
Zero-day exploits that are less than 30 days old.
Social engineering and phishing attacks.
Denial of Service (DoS) attacks.
Enumeration of email, phone number, or username information.
Known issues, duplicate submissions, or vulnerabilities already disclosed.
Physical attacks.
Vulnerabilities that can only be exploited in older versions of browsers or platforms.
Using known codebase vulnerabilities without actual proof.
Lack of security flags in cookies.
Issues related to insecure SSL/TLS sockets or protocol versions.
Content-based deception.
Cache management issues.
Internal IP or domain name leakages.
Missing security headers that cannot be directly exploited.
CSRF issues with negligible impact (such as adding to favorites, adding to cart, subscribing, etc.)
Issues without any security impact.
For any queries or submissions, please contact us at [email protected].
We look forward to your participation and thank you for helping us maintain a secure and trustworthy trading environment.
Last updated
